Securing 6G Network Slices with Closed-Loop Automation: 6G-OPENSEC-SECURITY in Action

As networks progress towards 6G, the complexity of multi-domain, multi-provider architectures calls for security solutions that are highly automated, interoperable, and resilient. The 6G-OPENSEC-SECURITY project leads this evolution by enabling automated creation and management of secure network slices, powered by Security SLAs (SSLAs) and closed-loop automation.
An Open and Automated Architecture for 6G Security
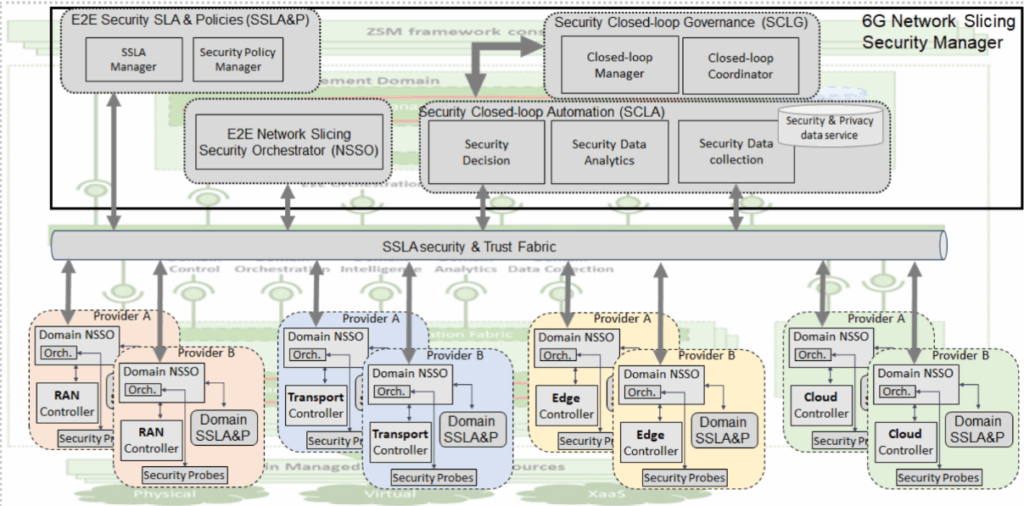
At the heart of the project is a framework that integrates Security Management Services using the ETSI ZSM principles: multilevel domain orchestration, integration fabric, and closed-loop control.
This architecture allows operators to define Security SLAs that are automatically translated into high-level security policies. These policies are enforced across different network segments—such as RAN, transport, edge, and even non-terrestrial networks—enabling the orchestration of end-to-end security slices.
Thanks to this automation, operators can ensure security requirements are fulfilled dynamically, efficiently, and at scale.
Innovations from the 6G-OPENSEC-SECURITY Project
The solution developed under the project includes:
- A Security SLA & Policies Manager (SSLAP) that translates SSLA templates into intent-based high-level policies.
- A Network Slicing Security Orchestrator (NSSO) that coordinates the deployment and enforcement of these policies across domains.
- A Closed-Loop Automation System that continuously monitors, analyzes, and responds to security events.
This entire framework is interoperable, modular, and designed to work with diverse providers and network types.
SSLA + Closed-Loop = End-to-End Security Automation
- Supports dynamic creation and orchestration of secure network slices.
- Converts high-level SSLA requirements into actionable configurations.
- Integrates with 6G-OPENSEC-TRUST for combined trust and security SLA enforcement.
- Facilitates detection, response, and mitigation of threats through automated closed-loop logic.
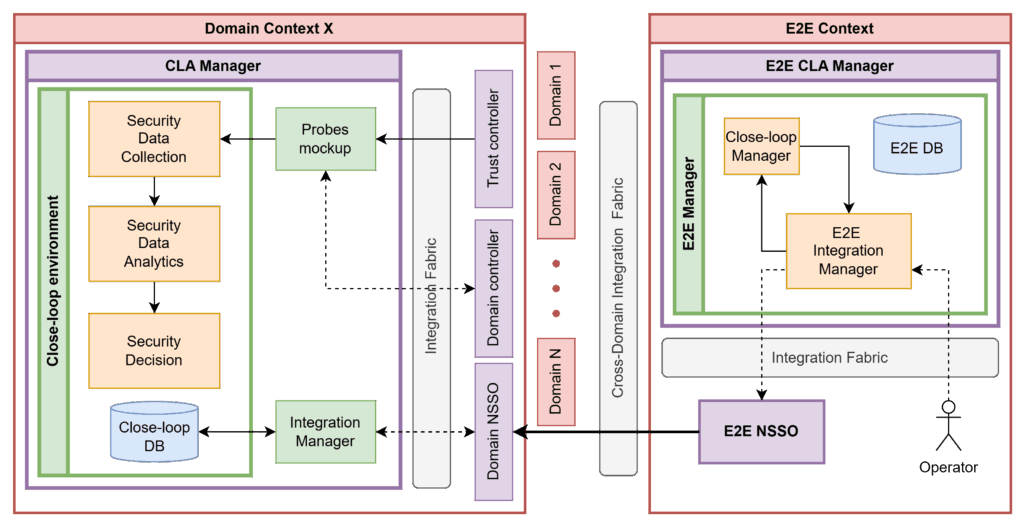
Closed-Loop Security Tools
- Security Decision (SD) evaluates threats and selects mitigation actions.
- Security Data Analytics (SDA) processes logs and metrics for threat detection, using ML models.
- Security Data Collection (SDC) interacts with probes and stores information in the Security & Privacy Data Service.
- E2E Closed-Loop Manager (CLM) coordinates all these modules to ensure timely and effective response, at E2E level.
These tools operate through standardized REST APIs and are fully auditable, traceable, and compliant with data privacy regulations.
Toward a Scalable and Interoperable Security Layer for 6G
The architecture allows:
- Operators to deploy security slices spanning multiple providers and domains with automated SLA enforcement.
- Vendors to integrate their security capabilities using exposed interfaces.
- Integrators to automate security deployments across complex 6G infrastructures.
This system enables resilient security responses and supports real-time alerts, smart contract integration, and even zero-knowledge proof validation for data confidentiality.
Commitment to a Secure and Trusted 6G Ecosystem
By providing an automated and standardized security framework, 6G-OPENSEC-SECURITY paves the way for a robust and trustworthy European 6G infrastructure. The integration with 6G-OPENSEC-TRUST ensures that both security and trust requirements are addressed holistically and effectively.
Acknowledgments:
The 6G-OPENSEC-SECURITY project (TSI-063000-2021-58) is funded by the Spanish Ministry for Economic Affairs and Digital Transformation and the European Union through the NextGenerationEU program, under the Recovery, Transformation and Resilience Plan and the Recovery and Resilience Facility.
Desafíos en el mercado mayorista de FTTH: Una perspectiva europea

Challenges in the FTTH wholesale market. A European perspective.